Пропала супруга Тимура Иванова? Женщину нигде не могут найти ни родственники, ни друзья https://t.co/p7t3QTo1i9 pic.twitter.com/2i0ropV9hu
— Michael Novakhov (@mikenov) April 26, 2024
Day: April 25, 2024
После задержания замминистра обороны Тимура Иванова пропала его супруга – Светлана Захарова. Об этом пишут различные телеграм-каналы. 50-летнюю женщину нигде не могут найти ни родственники, ни друзья.
После ареста Тимура Иванова в Сети сразу же появилась масса информации о том, что главный косвенный виновник того, что замминистра обороны вёл не до конца честный образ жизни, – это его жена Светлана Маниович (в девичестве Захарова). Маниович – это фамилия её бывшего супруга, после разрыва с которым она вышла замуж за Иванова.
Позже обиженный бывший муж в интервью СМИ рассказал о том, что виделся с Тимуром Ивановым, общался с ним по душам и отговаривал его жениться на Светлане, аргументируя это тем, что он попросту её “не потянет”:
Светлана требует минимум 50 000 долларов в месяц на содержание.
Как едко выразилось РИА “Катюша”, “бывшая жена олигарха Маниовича – эта дама известна всей Москве как скупщица тяжёлого люкса в особо крупных размерах и лютая тусовщица”.

СКРИНШОТ: COMPROMAT.RU
Но “потянуть” Тимур Иванов всё-таки смог. И помог ему не бизнес, а должность главного строителя в Министерстве обороны.
Если верить этой версии, то не исключено, что оплата аренды вилл, яхт, элитной недвижимости, покупка антиквариата и брендовой одежды могли стать причиной того, что замминистра оступился. При весьма невысокой официальной зарплате “потянуть” такое было невозможно.
Отсюда же вытекали мысли и о прозападной ориентации замминистра. “Тимур Иванов – очень прозападный человек, – сообщил источник “Досье”. – Уже будучи замминистра обороны и имея первую форму секретности, запрещающую поездки в страны НАТО, он сумел отметить свой день рождения на Лазурном берегу Франции”.

СКРИНШОТ: COMPROMAT.RU
Пара официально развелась в июне 2022 года, вскоре после начала СВО. Материалы на задержанного замминистра обороны Иванова собирали пять лет. Он не мог не знать, что под него копают. Можно предположить, что развод был необходим для того, чтобы перерегистрировать имущество на Светлану, то есть как раз вот для таких ситуаций, как произошла.
Вторая причина – вывести Светлану из-под санкций. Пишут, что она имеет гражданство Израиля, а её дети от первого брака уехали из России – сын отправился в Англию учиться за несколько дней до начала мобилизации, а его сестра живёт во Франции. Анекдотично, что сам Тимур Иванов курировал восстановление Мариуполя и создавал в России парк “Патриот”.
Несколько лет назад он отметил день рождения жены в Императорском яхт-клубе. На её 45-летии пели Вячеслав Бутусов, Гоша Куценко и Валерий Меладзе, писала газета Life. Издание отмечало, что соцсети Захаровой пестрят фотографиями с регулярных отпусков в Куршевеле, экзотических сафари в Африке, поездок в Сен-Тропе на открытие модных бутиков. В июне 2019-го появились сведения о том, что семья Иванова скрывает ряд объектов элитной недвижимости стоимостью в сотни миллионов рублей. Замминистра эту информацию оставил без комментариев.
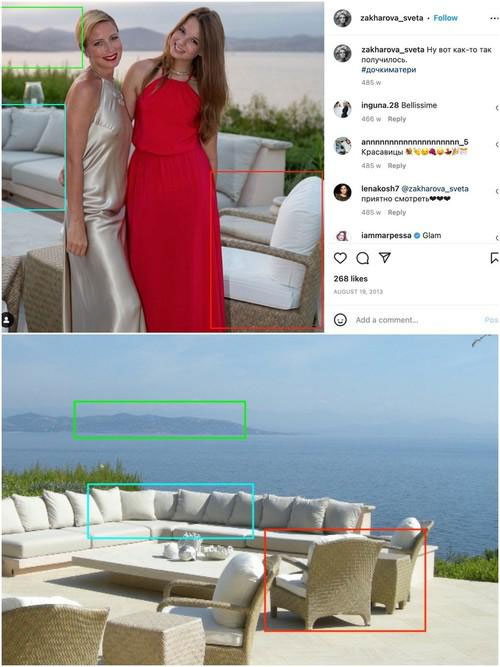
СКРИНШОТ: COMPROMAT.RU
Но ни одно ведомство, включая налоговую службу, так и не задало вопросов Тимуру Иванову. В настоящее время родственники и друзья Светланы Захаровой не могут связаться с ней и выражают озабоченность по поводу её местонахождения. Появилась версия, что Светлана могла быть задержана вместе со своим мужем. Правоохранительные органы пока не комментируют ситуацию. Хотя не исключено, что Захарова просто “легла на дно”.
тимур иванов – Google Search https://t.co/t2Wg1UE1MX – https://t.co/p7t3QTo1i9
— Michael Novakhov (@mikenov) April 26, 2024
Дело замминистра обороны Тимура Иванова. Что известно об арестованных – BBC News Русская служба https://t.co/o3AobZUU4o
— Michael Novakhov (@mikenov) April 26, 2024
Пропала бывшая жена арестованного замминистра обороны РФ: что известно о роскошной жизни Светланы Захаровой | https://t.co/dSKr51sJwR | Новости https://t.co/3rnuiGMd5l
— Michael Novakhov (@mikenov) April 26, 2024

Московский суд наложил обеспечительные меры на недвижимость, активы и банковские счета замминистра обороны РФ Тимура Иванова и его родственников.
«Все, что зарегистрировано на него и на его жену, а также на бывших жен и пятерых детей, включая приемных, все это имущество уже арестовано столичным судом в целях обеспечительных мер в случае признания Иванова впоследствии виновным», – рассказал собеседник ТАСС в правоохранительных органах.
23 апреля правоохранители прямо на рабочем месте задержали заместителя министра обороны России Тимура Иванова. Его обвинили в совершении преступления, предусмотренного статьей 290 (получение взятки в особо крупном размере) УК РФ. По версии следствия, Иванов вступил в преступный сговор с третьими лицами для получения взятки в особо крупном размере.
Басманный суд Москвы 24 апреля заключил Иванова под стражу. Суд арестовал также и Сергея Бородина, обвиняемого в соучастии при получении взятки Ивановым. По данным следствия, Бородин, находясь в дружеских связях с заместителем министра обороны РФ Ивановым, который курировал вопросы строительства и капитального ремонта объектов Минобороны, вступил в преступный сговор с третьими лицами, с которыми они объединились для получения взятки.
Иванов, которого называют самым богатым силовиком России, свою вину не признал. ФСБ заинтересовалось и доходами его семьи, в том числе его экс-супруги — светской львицы Светланы Захаровой.
После задержания Иванова его 50-летняя бывшая супруга Светлана Захарова пропала.
Сообщается, что Иванов в разводе с Захаровой с 2022 года. Бывшая супруга всегда вращалась в светских кругах. Сначала гражданка Израиля была замужем за миллиардером Михаилом Маниовичем, который признавался, что она требует от него на жизнь как минимум 50 тысяч долларов в месяц.
Материалы на задержанного замминистра обороны Иванова собирали пять лет. Он не мог не знать, что под него копают. Можно предположить: развод был необходим, чтобы перерегистрировать имущество на Светлану – как раз вот для таких ситуаций. Вторая причина – вывести ее из-под санкций.
Тимур Иванов — возможно, самый гламурный военный России. До войны в Украине он вместе со светской львицей и тогдашней женой Светланой Захаровой (Маниович) регулярно проводили отпуск в Сен-Тропе. На фото десятилетней давности Тимур Вадимович за рулем собственного Rolls Royce (оформлен на люксембургскую компанию, стоит 120 000 евро) катает Светлану по Лазурному берегу Франции, – пишут российские паблики.

Отсюда же вытекали мысли и о прозападной ориентации замминистра: «Тимур Иванов — очень прозападный человек. Уже будучи замминистра обороны и имея первую форму секретности, запрещающую поездки в страны НАТО, он сумел отметить свой день рождения на Лазурном берегу Франции».
В России Светлана Захарова вместе с отцом Тимура Иванова — Вадимом Ивановым является соучредителем (28% акций) компании «Кристалл Девелопмент», также ей принадлежит доля 33% в ООО «Частные технологии».
Иванов много лет вел роскошную светскую жизнь вместе со Светланой Маниович. В распоряжение журналистов в свое время попало множество счетов и чеков на аренду вилл (€120 тыс. в месяц), яхт (€90 тыс. в месяц), элитной недвижимости, организацию вечеринок по случаю дня рождения (€11 тыс. за вечер), массовую скупку антиквариата, брендовых вещей.
В настоящее время родственники и друзья Светланы Захаровой не могут связаться с ней и выражают озабоченность по поводу ее местонахождения. Появилась версия, что супруга могла быть задержана вместе со своим мужем. Правоохранительные органы пока не комментируют ситуацию.
Источники: ТАСС, Telegram- каналы ВЧК-ОГПУ, «Досье», Baza, ura.news, dzen.ru, lenta.ru.
https://t.co/CDCbQyGXV2 OSINT VS OSHIT #NewsAndTimes #NT #TNT #News #Times#World #USA #POTUS #DOJ #FBI #CIA #DIA #ODNI#Israel #Mossad #Netanyahu#Ukraine #NewAbwehr #OSINT#Putin #Russia #GRU #Путин, #Россия #SouthCaucasus #Bloggershttps://t.co/O0SIgLVWzM…
— Michael Novakhov (@mikenov) April 25, 2024
OSHIT: Seven Deadly Sins of Bad Open Source Research, and other Selected Articles https://t.co/K1eGSDjkey pic.twitter.com/H65fSEaxj1
— Michael Novakhov (@mikenov) April 25, 2024
Michael Novakhov’s favorite articles on Inoreader
When news breaks and the internet is aflutter with activity and speculation, many turn to open source accounts and experts to make sense of events. This is truly a sign that open source research — using resources like satellite images to flight tracking websites and footage recorded on the ground — is seen as credible and is increasingly sought after. It’s free, publicly available and anybody can do it.
But such success comes with drawbacks. In monitoring events from Iran and Ukraine, this surge in credibility allows the term ‘OSINT’ to be easily abused, either knowingly or unknowingly, by users who don’t actually follow the best practice of open source research methods. In fact, since the start of the war in Gaza in October 2023, there has been a spike in verified ‘OSINT’ Twitter accounts which create additional noise and confusion with poor open source analysis.
Conducting open source research properly isn’t about being ‘verified’ or having a huge following. It isn’t about expecting people to take your word for things. It’s about collaboration and sharing the skills necessary to independently verify what you see online. It’s about showing your working and the origin of your data so that anybody can replicate your methodology.
As Bellingcat’s Giancarlo Fiorella indicated in the Financial Times in December, open source research is critical in the long term when it could come to play a role in prosecuting those responsible for atrocity crimes. That raises the bar significantly — not just for the sake of the open source research community as a whole, but also for that of accountability for the victims of armed conflicts.
Here are a few mistakes we’ve noticed from open source researchers in recent years. Many examples are relevant to monitoring armed conflict, but could broadly apply to any genre on which open source research shines — such as natural disasters or organised crime.
We work in a young and rapidly evolving field, facing a deluge of information. Mistakes should be no cause for surprise or shame. Everybody makes them. But a good open source researcher is open about doing so – they correct their errors quickly and vow to do better next time.
If you’re a reader, looking out for these ‘Seven Sins’ (listed in no particular order of gravity) will help you independently judge the quality of open source research you encounter online. If you’re also an open source researcher, looking out for them will help improve the quality of your own work.

Collage by Bellingcat. Images taken from various Bellingcat investigations between 2021 and 2024
1. Not Providing the Original Source
The main tenet of open-source research is that it’s ‘open’: ideally the information is publicly accessible and used in a transparent way. This allows anyone to verify the sourcing and veracity of a piece of footage, without having to trust the person who posted it.
In the wake of Russia’s full-scale invasion of Ukraine in 2022, many “OSINT aggregator” accounts developed large followings on Twitter, mostly reposting videos from Telegram, often without linking to the video’s original source. When someone posts a video without saying where they got it from, verification becomes much more difficult; researchers can’t just follow a chain of links to its origin.
Without any clues as to who originally uploaded that video, we lose potentially crucial information about its content. Though most social media platforms strip metadata, for some platforms such as Telegram and Parler retain it. Such image metadata has played important roles in Bellingcat investigations on subjects from QAnon’s origins to Russian disinformation in Ukraine. This means that first instance of a photo or video may also contain metadata which is lost when the content is reuploaded, shared or compressed.
Bear in mind that there are circumstances when it can be ethically fraught to provide a link, such as if doing so would amplify hateful accounts or drive traffic to graphic content content. Nevertheless, a rule of thumb is to share when you can.
That’s because sharing the origin of a piece of content is a greater contribution than keeping it to yourself — the better to hoard future ‘discoveries’.
2. Letting Cheerleading Undermine Your Work
While everyone has bias, it’s important for open source researchers to attempt to separate these biases from the evidence that they examine. Though many open source researchers or communities clearly use these techniques in aid of a certain cause, they should still acknowledge when their sources or research don’t support that cause, and always be transparent about the level of uncertainty.
Confirmation bias is our tendency to accept as true any new information that confirms what we already ‘know’ to be true, and to reject new information that contradicts our beliefs. Just as everyone has bias, everyone is liable to fall victim to confirmation bias.
Nevertheless, the quality of open source research can be judged independently of political or social position. This is why the caveats are so important. Open source information doesn’t show everything, and may not prove whatever larger point you would like it to.
Acknowledging what you don’t know and what you can’t know is crucial for building trust — even if you have very clear and very public positions. Failing to do this can result in erroneous and self-serving investigations.
3. Not Archiving Material
Online content is often ephemeral: the internet is littered with links to pages that no longer exist. This could be because the owner of the web domain stopped paying their bills. It could be because the website changed how they organised pages. A content hosting platform could have decided to delete large amounts of their files, whether on purpose or by accident. Social media posts are often deleted, whether by the account who created the post, or by the social media platform’s moderation team.
That makes the work of open source researchers much more difficult. It’s why Bellingcat frequently emphasises the importance of archiving online content and has developed tools for making this easier.
The most trustworthy way to archive content is with third-party archiving platforms like the Internet Archive’s Wayback Machine or archive.today, though they often fail to correctly archive content from several social media platforms, as well as videos in general. If all else fails, a screenshot is better than nothing.
4. Lacking Context for Occurrences, Common or Otherwise
Particularly in the context of conflict monitoring, events that occur on a regular basis are often taken out of their original context and overblown. For example, researchers unfamiliar with reading NASA FIRMS images and data, may interpret regular, planned and controlled fires or other thermal changes as something more malicious. But in moments of geopolitical tension, people unfamiliar with such common events may give them undue significance.
Screenshot of a post from Twitter/X fuelling an unfounded rumour about Prime Minister Netanyahu’s location prior to Iran’s recent missile attack on Israel based on flight data of a government plane. Bellingcat has obscured the account’s name
A recent example of this was when famous baseball player Shohei Ohtani, was going to join a new team, leaving the Los Angeles Angels. In December 2023, a private flight leaving Anaheim in the US state of California for Toronto, Canada spurred online sleuths to believe that this was evidence of Ohtani meeting and potentially signing with the Toronto Blue Jays. when In reality, the flight was carrying a Canadian businessman and had no connection to Ohtani or baseball in general.
Distinguishing between common and uncommon events can take a lot of domain-specific expertise, whether that field is conflict monitoring, natural disasters, or any other area of research. Many researchers do not have this specific expertise regardless of how well they have mastered a tool or method.
5. Incorrectly Using Tools and Interpreting Data
There are many different open source tools out there, and in fact, we even try to keep a list of useful resources in Bellingcat’s Online Investigation Toolkit. However, as with any new tool, users often need some guidance, experience and training to master it.
We often see new users not being aware of these tools’ limitations. New tools aren’t silver bullets and they often come with many caveats. For example, for facial recognition software, there are strengths and weaknesses for different services and results provided by those tools should not be treated with complete certainty. Usually other data points and context is required to show why the match is credible. Depending on the photo and the particular case, it is possible to pursue false leads and come to incorrect conclusions based on the limitations of that software.
Tools which detect photo manipulation are another example. Last May, Colombia’s president retweeted an account who had improperly used one such tools, drawing overconfident and incorrect conclusions.
Even when such tools have been mastered, it takes time to learn how to interpret the data or results they generate. In one example, drone footage of a fast moving was interpreted as a UFO when in reality, it may have just been a balloon.
In another, a user mistook clouds on satellite imagery for craters.
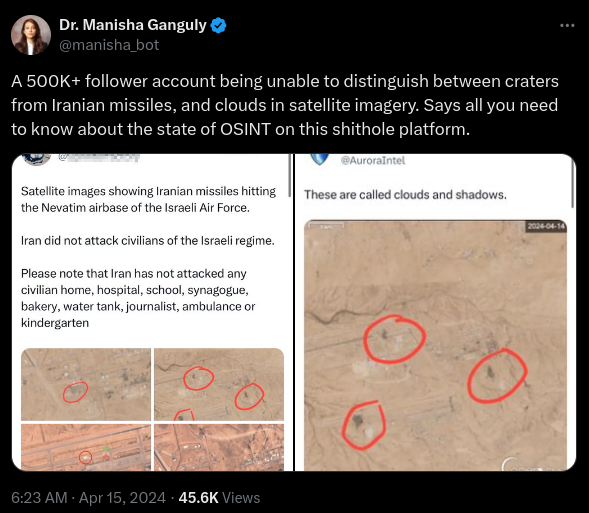
Screenshot of post from investigative journalist Manisha Ganguly on X/Twitter showing the misidentification of clouds as missile damage from an Iranian missile strike. Original username obscured by Bellingcat.
6. Editing Footage
While usually not done maliciously, OSINT accounts sometimes edit footage in an unhelpful way, such as placing an audio track over the video, making a compilation of clips, or trimming down the original footage.
For example, one habit of ‘aggregator’ accounts is to overlay their channel’s watermark over videos and images. If we can’t find the origin of a video, we generally perform a reverse image search of frames from the footage. But thanks to watermarks, this useful technique becomes more prone to error.

Example of a gratuitously watermarked image, based on a photo from a recent Bellingcat investigation into narco kingpin Christy Kinahan. This editing is only slightly exaggerated when compared to the watermarking practices of some users’ accounts. Such practices often make verification and image analysis more difficult.
When interpreting and sharing open source content, it is critical that we do not edit the footage in a way that diminishes, removes, or obscures useful information contained in that content. Even if you think you are not obscuring critical information, there is no way to know if the information you altered would be helpful later.
For example, the audio contained in the footage of the shooting of Columbian journalist Abelardo Liz contained vital clues that allowed us to geolocate where the gunfire came from. If this footage was edited over with a dramatic audio track, it would have concealed a vital component of this investigation.
7. Racing to be First at Any Cost
It is easy to get wrapped up in the whirlwind of breaking news, especially around terror attacks and military conflict. The incentives of social media platforms, where the bulk of public open source research is carried out, encourage this behaviour. There is a big temptation to be the first person to make a ‘breakthrough’ in a developing story, or to quickly generate an analysis on an event.
However, validating content should always take priority over speed.
Some of the most high-profile and damaging examples of this are the many times that amateur investigators misidentified innocent people as the perpetrators of terror attacks. This occurred recently with the Bondi Junction stabbing, as well as the Boston Marathon bombings in 2013 and the Allen, Texas mall shooting in 2023. These kinds of mistaken results have been based on the innocent person having the same name or a similar looking face as the perpetrator — neither of which is sufficient evidence alone given the gravity of such identifications.
Too often, verification gets overlooked when the desire for speed is prioritised which can create more harm and confusion about an unfolding situation rather than bringing the facts and clarity needed.
Bellingcat is a non-profit and the ability to carry out our work is dependent on the kind support of individual donors. If you would like to support our work, you can do so here. You can also subscribe to our Patreon channel here. Subscribe to our Newsletter and follow us on Instagram here, X here and Mastodon here.
The post OSHIT: Seven Deadly Sins of Bad Open Source Research appeared first on bellingcat.
Learn more about sponsor message choices: podcastchoices.com/adchoices
New York City Council legislation introduced in response to the partial building collapse in the Bronx last December aims to create stricter oversight on landlords and a stronger building inspection protocol.
 Соединенные Штаты готовятся объявить один из крупнейших в истории пакетов военной помощи для Украины в рамках программы USAI. Общая сумма предоставленного пакета составит 6 миллиардов долларов США. Полный текст новости
Соединенные Штаты готовятся объявить один из крупнейших в истории пакетов военной помощи для Украины в рамках программы USAI. Общая сумма предоставленного пакета составит 6 миллиардов долларов США. Полный текст новости
Russia’s deputy defense minister was arrested Tuesday evening on bribery charges, but some analysts have speculated the detainment of Timur Ivanov was a warning to his boss, Defense Minister Sergei Shoigu.
Russian President Vladimir Putin “doesn’t sign off on that [arrest] unless he’s sending a message to Shoigu, one that reads something along the lines of ‘that could have been you,'” David Silbey, associate professor of history at Cornell and director of teaching and learning at Cornell in Washington, told Newsweek.
On Wednesday, Shoigu removed Ivanov from his post as deputy defense minister, according to Kremlin-controlled news agency TASS. Hours earlier, reports emerged of Ivanov’s arrest on accusations that he had been taking bribes on what a Moscow court called “a particularly large scale.” He could face 15 years in prison.
Prior to the arrest, Ivanov was in charge of Russian military infrastructure projects. Perhaps more importantly, he was widely seen as one of Shoigu’s closest allies. The two men had worked together for many years, including when Ivanov served as deputy prime minister of the Moscow region while Shoigu was the area’s governor.
Newsweek reached out to the Kremlin and the Russian Ministry of Defense on Wednesday via email for comment.

Russian President Vladimir Putin, left, talks to Defense Minister Sergei Shoigu during a ceremony on February 23 in Moscow. Russia’s deputy defense minister was arrested Tuesday night on bribery charges, leading to speculation that Putin… Russian President Vladimir Putin, left, talks to Defense Minister Sergei Shoigu during a ceremony on February 23 in Moscow. Russia’s deputy defense minister was arrested Tuesday night on bribery charges, leading to speculation that Putin was sending a message to Shoigu. Photo by Contributor/Getty Images
The Kremlin has denied early reports that Ivanov’s arrest was related to treason, but not everyone is convinced about Russia’s official line regarding Ivanov’s detention.
“Since corruption among top Russian officials is endemic, it’s hard to believe that the arrest of Shoigu’s deputy is just about corruption,” George Mason University Schar School of Policy and Government professor Mark N. Katz told Newsweek.
He continued, “Either he has done something else that someone opposed, or it is a move aimed at weakening Shoigu—or both.”
Shoigu has frequently been blamed for Russia’s shortcomings on the battlefield in Ukraine, including by former Wagner Group leader Yevgeny Prigozhin, who perished in a plane crash under mysterious circumstances after leading a mutiny against Moscow. Katz said the incident reminded him of the public feud between Shoigu and Prigozhin.
“The arrest harkens back to Prigozhin’s criticism last year of incompetence within the top Russian military leadership. Prigozhin is gone, but the problems he publicized remain,” Katz said.
“The real issue is not whether the deputy minister is corrupt. It is instead whether he, and—more to the point—Shoigu, have become centers of power in their own right,” William Reno, professor and chair of the political science department at Northwestern University, told Newsweek.
“Corruption in the current regime is a strategic asset that’s tolerated and even encouraged to cultivate a person’s loyalty and dependence on the political leadership and then used against them when they become a threat or need to be used as a convenient target of blame for the regime’s shortcomings,” Reno said. “Charging him with corruption at this juncture helps to undermine public trust and support for his boss, Shoigu.
“Charging a high official with corruption also highlights Putin’s sovereign right as leader to punish, reinforcing his authority among his subordinates and in the eyes of Russian citizens.”
Ivanov’s arrest may just be the beginning of what’s to come for Shoigu, according to Silbey.
“Remember that being ‘too powerful’ isn’t a deterrent to Putin (or any dictator) taking someone out, it’s an incentive,” he said. “The more powerful someone is, the more they’re an existential threat to the dictator. Joseph Stalin’s golden rule was ‘do unto others before they do it to you.'”
“It would not surprise if Shoigu is next or retires suddenly,” Silbey added.
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.

 image/jpeg 470621.jpg
image/jpeg 470621.jpgRussia’s well-connected deputy defense minister Timur Ivanov faces accusations of treason it has been reported, following his arrest in the highest-profile corruption scandal in Russia for years.
Ivanov, 48, an official responsible for military infrastructure projects, appeared in his uniform behind a glass cage in Moscow’s Basmanny Court on Wednesday charged with bribe-taking “on a particularly large scale,” the court’s press service said. He could face 15 years in prison.
His arrest has sparked speculation about whether it might signal a purge among the Moscow elite, especially given his close relationship with defense minister Sergei Shoigu, and Kremlin spokesman Dmitry Peskov.
The independent Russian news outlet Real Stories said that the true reason for Ivanov’s arrest was “high treason,” citing two sources close to the FSB.

This handout from Moscow’s Basmanny District Court from April 24, 2024, shows Russian deputy defense minister Timur Ivanov. He was detained on suspicion of bribery. This handout from Moscow’s Basmanny District Court from April 24, 2024, shows Russian deputy defense minister Timur Ivanov. He was detained on suspicion of bribery. Getty Images
“A bribe is for the public. So far, they don’t want to talk publicly about treason—it’s a big scandal,” one source told the outlet. A second source said that Putin “gave the command after being convinced it was about treason,” adding that “no one would detain Ivanov for corruption.”
However, Ivanov’s lawyer, Murad Musayev, told state news agency RIA Novosti, that his client was not being accused of treason.
“There are no other accusations, except for the announced accusation of bribery,” he said.
Newsweek has contacted the court for comment.
Independent Russian media outlets have alleged that Ivanov and his family had acquired vast wealth through kickbacks on contracts he agreed at the ministry.
In December 2022, the anti-corruption organization, FBK, founded by the late Russian opposition figure Alexei Navalny, who died in custody in February, alleged that Ivanov and his family lived an opulent life abroad that included luxury cars, jewelry and expensive real estate.
Navalny’s team also said that Ivanov had profited from construction projects in the Ukrainian city of Mariupol, which fell under Moscow’s control after a monthslong siege.
Deputy defense minister since 2016, Ivanov’s projects also included building military barracks, cadet corps, submarine bases and military airfields, as well as hospitals and kindergartens, it was reported.
“Timur Ivanov is a high-profile figure in Russia, and he’s been involved in many large projects, including several rebuilding efforts in Mariupol,” Pekka Kallioniemi, a postdoctoral researcher at Finland’s Tampere University, told Newsweek.
“It’s of course impossible to know the real reasons for his arrest but this could be related to the revelations made by Navalny’s Anti-Corruption Foundation that showed Ivanov and his wife in a pretty bad light,” Kallioniemi said.
FBK alleged leaked emails from Ivanov’s wife, Svetlana Maniovich, showed the extent of her family’s lavish lifestyle, beyond what his official salary could cover, with some transactions routed through third parties, including Defense Ministry contractors.
“As the couple is also close friends with Dmitry Peskov, this is one of the highest profile arrests after Russia launched their full-scale invasion against Ukraine in February of 2022,” said Kallioniemi, whose series on social media, Vatnik Soup, exposed Russian propaganda.
When asked about the arrest, which took place only hours after Ivanov had met with Shoigu and other defense ministry officials, Peskov told reporters on Wednesday that there were “many different interpretations” of the case, state news agency Tass reported.
“All this speculation is nothing but speculation,” he said. “It is necessary to be guided by information from the investigative authorities. And, of course, in the end, the court’s decision.”
Ivanov has been remanded to Moscow’s Lefortovo pre-trial detention center until June 23.
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
When news breaks and the internet is aflutter with activity and speculation, many turn to open source accounts and experts to make sense of events. This is truly a sign that open source research — using resources like satellite images to flight tracking websites and footage recorded on the ground — is seen as credible and is increasingly sought after. It’s free, publicly available and anybody can do it.
But such success comes with drawbacks. In monitoring events from Iran and Ukraine, this surge in credibility allows the term ‘OSINT’ to be easily abused, either knowingly or unknowingly, by users who don’t actually follow the best practice of open source research methods. In fact, since the start of the war in Gaza in October 2023, there has been a spike in verified ‘OSINT’ Twitter accounts which create additional noise and confusion with poor open source analysis.
Conducting open source research properly isn’t about being ‘verified’ or having a huge following. It isn’t about expecting people to take your word for things. It’s about collaboration and sharing the skills necessary to independently verify what you see online. It’s about showing your working and the origin of your data so that anybody can replicate your methodology.
As Bellingcat’s Giancarlo Fiorella indicated in the Financial Times in December, open source research is critical in the long term when it could come to play a role in prosecuting those responsible for atrocity crimes. That raises the bar significantly — not just for the sake of the open source research community as a whole, but also for that of accountability for the victims of armed conflicts.
Here are a few mistakes we’ve noticed from open source researchers in recent years. Many examples are relevant to monitoring armed conflict, but could broadly apply to any genre on which open source research shines — such as natural disasters or organised crime.
We work in a young and rapidly evolving field, facing a deluge of information. Mistakes should be no cause for surprise or shame. Everybody makes them. But a good open source researcher is open about doing so – they correct their errors quickly and vow to do better next time.
If you’re a reader, looking out for these ‘Seven Sins’ (listed in no particular order of gravity) will help you independently judge the quality of open source research you encounter online. If you’re also an open source researcher, looking out for them will help improve the quality of your own work.

Collage by Bellingcat. Images taken from various Bellingcat investigations between 2021 and 2024
1. Not Providing the Original Source
The main tenet of open-source research is that it’s ‘open’: ideally the information is publicly accessible and used in a transparent way. This allows anyone to verify the sourcing and veracity of a piece of footage, without having to trust the person who posted it.
In the wake of Russia’s full-scale invasion of Ukraine in 2022, many “OSINT aggregator” accounts developed large followings on Twitter, mostly reposting videos from Telegram, often without linking to the video’s original source. When someone posts a video without saying where they got it from, verification becomes much more difficult; researchers can’t just follow a chain of links to its origin.
Without any clues as to who originally uploaded that video, we lose potentially crucial information about its content. Though most social media platforms strip metadata, for some platforms such as Telegram and Parler retain it. Such image metadata has played important roles in Bellingcat investigations on subjects from QAnon’s origins to Russian disinformation in Ukraine. This means that first instance of a photo or video may also contain metadata which is lost when the content is reuploaded, shared or compressed.
Bear in mind that there are circumstances when it can be ethically fraught to provide a link, such as if doing so would amplify hateful accounts or drive traffic to graphic content content. Nevertheless, a rule of thumb is to share when you can.
That’s because sharing the origin of a piece of content is a greater contribution than keeping it to yourself — the better to hoard future ‘discoveries’.
2. Letting Cheerleading Undermine Your Work
While everyone has bias, it’s important for open source researchers to attempt to separate these biases from the evidence that they examine. Though many open source researchers or communities clearly use these techniques in aid of a certain cause, they should still acknowledge when their sources or research don’t support that cause, and always be transparent about the level of uncertainty.
Confirmation bias is our tendency to accept as true any new information that confirms what we already ‘know’ to be true, and to reject new information that contradicts our beliefs. Just as everyone has bias, everyone is liable to fall victim to confirmation bias.
Nevertheless, the quality of open source research can be judged independently of political or social position. This is why the caveats are so important. Open source information doesn’t show everything, and may not prove whatever larger point you would like it to.
Acknowledging what you don’t know and what you can’t know is crucial for building trust — even if you have very clear and very public positions. Failing to do this can result in erroneous and self-serving investigations.
3. Not Archiving Material
Online content is often ephemeral: the internet is littered with links to pages that no longer exist. This could be because the owner of the web domain stopped paying their bills. It could be because the website changed how they organised pages. A content hosting platform could have decided to delete large amounts of their files, whether on purpose or by accident. Social media posts are often deleted, whether by the account who created the post, or by the social media platform’s moderation team.
That makes the work of open source researchers much more difficult. It’s why Bellingcat frequently emphasises the importance of archiving online content and has developed tools for making this easier.
The most trustworthy way to archive content is with third-party archiving platforms like the Internet Archive’s Wayback Machine or archive.today, though they often fail to correctly archive content from several social media platforms, as well as videos in general. If all else fails, a screenshot is better than nothing.
4. Lacking Context for Occurrences, Common or Otherwise
Particularly in the context of conflict monitoring, events that occur on a regular basis are often taken out of their original context and overblown. For example, researchers unfamiliar with reading NASA FIRMS images and data, may interpret regular, planned and controlled fires or other thermal changes as something more malicious. But in moments of geopolitical tension, people unfamiliar with such common events may give them undue significance.
Screenshot of a post from Twitter/X fuelling an unfounded rumour about Prime Minister Netanyahu’s location prior to Iran’s recent missile attack on Israel based on flight data of a government plane. Bellingcat has obscured the account’s name
A recent example of this was when famous baseball player Shohei Ohtani, was going to join a new team, leaving the Los Angeles Angels. In December 2023, a private flight leaving Anaheim in the US state of California for Toronto, Canada spurred online sleuths to believe that this was evidence of Ohtani meeting and potentially signing with the Toronto Blue Jays. when In reality, the flight was carrying a Canadian businessman and had no connection to Ohtani or baseball in general.
Distinguishing between common and uncommon events can take a lot of domain-specific expertise, whether that field is conflict monitoring, natural disasters, or any other area of research. Many researchers do not have this specific expertise regardless of how well they have mastered a tool or method.
5. Incorrectly Using Tools and Interpreting Data
There are many different open source tools out there, and in fact, we even try to keep a list of useful resources in Bellingcat’s Online Investigation Toolkit. However, as with any new tool, users often need some guidance, experience and training to master it.
We often see new users not being aware of these tools’ limitations. New tools aren’t silver bullets and they often come with many caveats. For example, for facial recognition software, there are strengths and weaknesses for different services and results provided by those tools should not be treated with complete certainty. Usually other data points and context is required to show why the match is credible. Depending on the photo and the particular case, it is possible to pursue false leads and come to incorrect conclusions based on the limitations of that software.
Tools which detect photo manipulation are another example. Last May, Colombia’s president retweeted an account who had improperly used one such tools, drawing overconfident and incorrect conclusions.
Even when such tools have been mastered, it takes time to learn how to interpret the data or results they generate. In one example, drone footage of a fast moving was interpreted as a UFO when in reality, it may have just been a balloon.
In another, a user mistook clouds on satellite imagery for craters.

Screenshot of post from investigative journalist Manisha Ganguly on X/Twitter showing the misidentification of clouds as missile damage from an Iranian missile strike. Original username obscured by Bellingcat.
6. Editing Footage
While usually not done maliciously, OSINT accounts sometimes edit footage in an unhelpful way, such as placing an audio track over the video, making a compilation of clips, or trimming down the original footage.
For example, one habit of ‘aggregator’ accounts is to overlay their channel’s watermark over videos and images. If we can’t find the origin of a video, we generally perform a reverse image search of frames from the footage. But thanks to watermarks, this useful technique becomes more prone to error.

Example of a gratuitously watermarked image, based on a photo from a recent Bellingcat investigation into narco kingpin Christy Kinahan. This editing is only slightly exaggerated when compared to the watermarking practices of some users’ accounts. Such practices often make verification and image analysis more difficult.
When interpreting and sharing open source content, it is critical that we do not edit the footage in a way that diminishes, removes, or obscures useful information contained in that content. Even if you think you are not obscuring critical information, there is no way to know if the information you altered would be helpful later.
For example, the audio contained in the footage of the shooting of Columbian journalist Abelardo Liz contained vital clues that allowed us to geolocate where the gunfire came from. If this footage was edited over with a dramatic audio track, it would have concealed a vital component of this investigation.
7. Racing to be First at Any Cost
It is easy to get wrapped up in the whirlwind of breaking news, especially around terror attacks and military conflict. The incentives of social media platforms, where the bulk of public open source research is carried out, encourage this behaviour. There is a big temptation to be the first person to make a ‘breakthrough’ in a developing story, or to quickly generate an analysis on an event.
However, validating content should always take priority over speed.
Some of the most high-profile and damaging examples of this are the many times that amateur investigators misidentified innocent people as the perpetrators of terror attacks. This occurred recently with the Bondi Junction stabbing, as well as the Boston Marathon bombings in 2013 and the Allen, Texas mall shooting in 2023. These kinds of mistaken results have been based on the innocent person having the same name or a similar looking face as the perpetrator — neither of which is sufficient evidence alone given the gravity of such identifications.
Too often, verification gets overlooked when the desire for speed is prioritised which can create more harm and confusion about an unfolding situation rather than bringing the facts and clarity needed.
Bellingcat is a non-profit and the ability to carry out our work is dependent on the kind support of individual donors. If you would like to support our work, you can do so here. You can also subscribe to our Patreon channel here. Subscribe to our Newsletter and follow us on Instagram here, X here and Mastodon here.
The post OSHIT: Seven Deadly Sins of Bad Open Source Research appeared first on bellingcat.
